Cybercriminals are constantly developing new ways to exploit the system. It’s hard to fathom why they wouldn’t put their intelligence to better use. However, this post is not about praising criminals’ intelligence. It’s about a new Android malware known as FjordPhantom.
The malware is reported to be causing chaos in Asian countries such as Indonesia, Thailand, Vietnam, Singapore, and Malaysia. One victim was defrauded of 10 million Thai Baht, which is approximately $280,000.
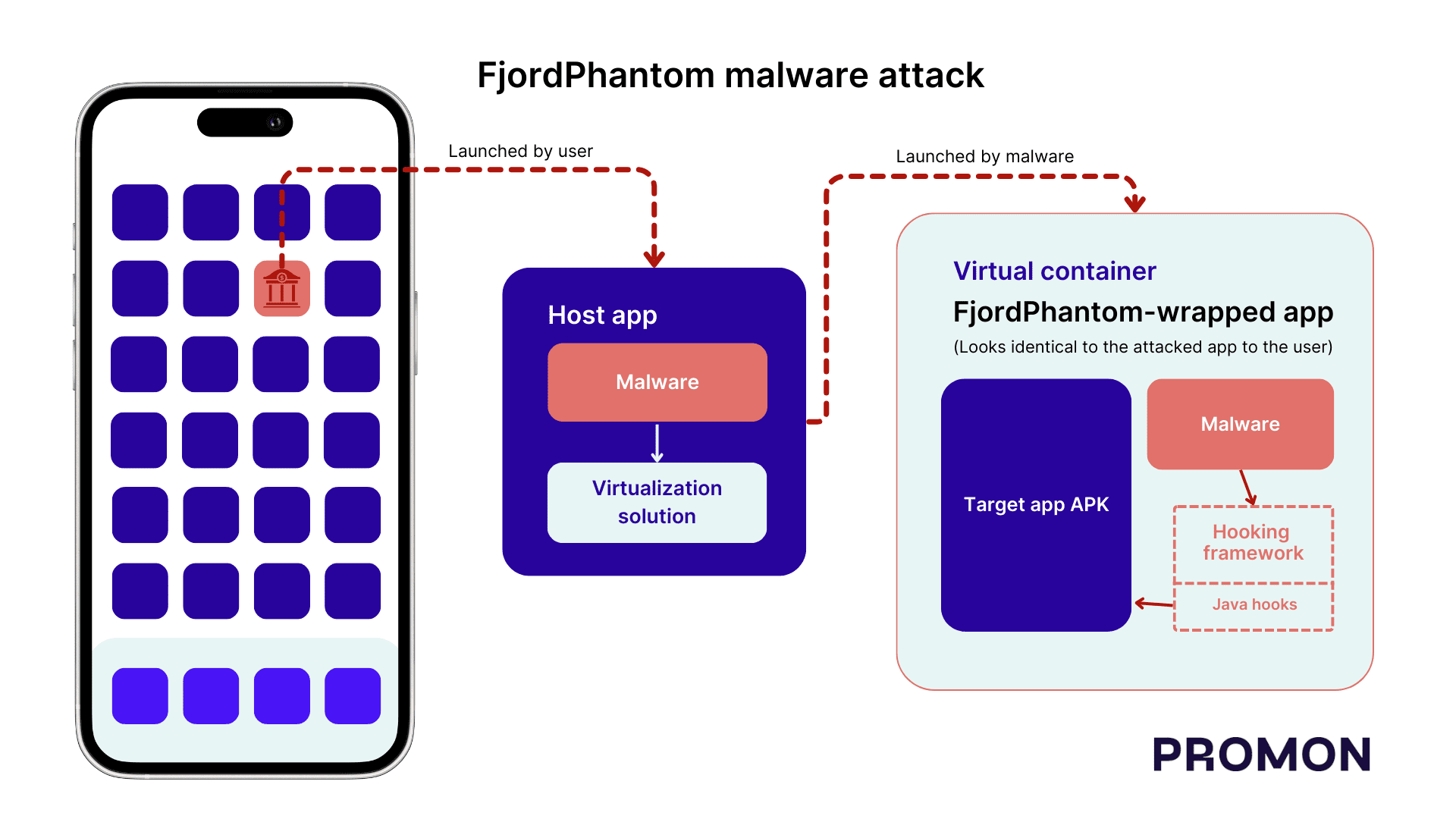
The attack begins with the victim receiving an email or message containing a prompt to download a legitimate banking app. However, once the app is downloaded, it runs in a virtual environment, allowing attackers to take control of the device. Virtualization provides a private execution environment for running code, allowing activities such as downloading the same app twice for use by two users sharing the same device.
There’s also a social engineering element to the attack: after the app is downloaded, cybercriminals call the victim, impersonating a customer service representative from the bank to assist with running the app. This step helps the attacker deceive the victim into conducting a transaction or disclosing credentials.
By downloading a legitimate app into a virtual file system and using hooking, FjordPhantom disrupts the normal handling of an app by Android to avoid detection of any suspicious activity.
Since the app is installed in a virtual container, it bypasses the Android sandbox, a security feature that isolates an app’s code and data from other apps and the system. Without sandboxing, apps can access each other’s files, inject code into each other, and eliminate the need for root access and root detection.
Experts believe that FjordPhantom will continue to evolve. To protect yourself, ensure that you only download apps from trusted sources and refrain from sharing sensitive information over the phone, even if the caller claims to be from your bank, as banks typically do not request such information over the phone.











